Abstract
Within this paper, we advise a biometric-based attendance system for course lecture. The proposal system takes attendance during lecture periods instantly using student identification method. Efforts within this work recorded 94% rate of success for eight students who took part in the research. Biometrics based attendance system created roughly 3.8 seconds execution time around the average as the manual approach to attendance created roughly 17.8 seconds execution time around the average. Outcomes of the biometric based attendance system confirm improved performance than the manual approach to attendance. Continuous observation improved the performance.
Instantly: Figures
- Figure1. Various biometric modalities: Fingerprints, Speech, Handwriting, Facial Recognition, Hands Geometry and Chemical Biometrics”>
1. Introduction
Using biometric technology attending management can’t be overemphasized. Biometric is definitely an automated of recognizing an individual according to physiological or behavior characteristics. Many biometrics can be used as some specific systems but nevertheless the same. From literature you are able to that biometrics can be used for objective identification and verification.
Every Nigerian college has got the obligation to record and take student attendance during lecture periods every semester. The precision of the record of attendance as essential as it’s happen to be damaged by many people challenging problems which varies from the cumbersome nature from the paper sheets utilized in recording, manipulation from the attendance record by fraudulent students, emplacement from the attendance records after taking them and so forth.
Choice becomes very hard for that regular management increase of these records that have been formerly taken. Even the calculation from the number of attendance to determine the qualification of student to create a specific examination might not be achieved. For that mentioned reasons, a biometric based attendance product is developed and made to overcome the issues connected using the attendance system. Biometric-based systems are particularly employed for among the two identified objectives including verification and identification. Identifications suggests a match between your query biometric is one of the claimed identity or otherwise. Formerly biometric techniques were utilized in many areas for example charge cards, passport control, criminal investigations, ATM and security services.
This biometric based system we suggested within this work uses finger marks technique. It’s been noticed in literature that people have used fingerprints for recognition for any lengthy time, because of its simplicity and precision. The developed system assists you to estimate instantly whether each student exists or absent as well as create the percentage on to determine eligibility for examination inside a particular course.
Benefits of Biometrics include:
• Precision and Security: tokens for example papers, keys, magnetic stripe cards could be lost, stolen or duplicated passwords might be shared.

On other hands, biometric verification requires the physical existence of the consumer.
• Screening: in biometrics, users can’t assume multiple identities and therefore it will help to screen you [1 ] .
• Non-repudiation: along with other security models, perpetrators can deny committing a specific action. Biometrics [2 ] completely eliminates the issue of repudiation.
• Universality: everybody includes a biometric feature which is thus universal to everyone.
• Atmosphere friendly: it cuts down on paper along with other resource requirement and doesn’t cause any negative impact towards the atmosphere.
The different biometric modalities could be categorized as
• Behavioural Biometrics: these involve calculating the way a person functions, reactions and also the aggregate from the responses or movements produced by the consumer. Including signature, gait, key stroke dynamics, speech et.c
• Physical Biometrics: these involve all types of physical measurements and the body characteristics that differ for every person for example facial recognition, fingerprints, hands geometry, iris recognition et.c
• Chemical Biometrics: it is really an emerging field of biometric also it involves calculating cues like the chemical composition of human perspiration, body odour et.c
Figure1. Various biometric modalities: Fingerprints, Speech, Handwriting, Facial Recognition, Hands Geometry and Chemical Biometrics
A biometric system may either be an identification system or perhaps a verification system (authentication) system, with respect to the application [3 ]. Identification and Verification can be explained as [4 ] :
• Identification–Someone to Many: identification involves figuring out a person’s identity by looking through the database for any match (Essentially, the machine attempts to answer the issue, “Who shall we be held?”). For instance, identification is conducted inside a list to locate when the query image matches with the images within the list it’s also utilized by police force agencies for criminal identification initiatives to link a suspect for an unsolved crime or find out the person suspected of committing a criminal offense.
• Verification–Face to face: verification involves figuring out when the identity that the individual is claiming is true or otherwise (Essentially, the machine attempts to answer the issue, “Am I whom I tell you they are?”). Types of verification include use of an ATM it may be acquired by matching the characteristics from the claimed identity within the database (a person might tell you they are matric no 050210057 by presenting his identity using his fingerprint). It’s not needed to do complement complete database.
There’s two major kinds of biometric systems: unimodal and multimodal systems. Unimodal biometric systems are just one characteristic or feature for recognition for example face recognition, fingerprint recognition, and iris recognition. Multimodal biometric systems typically use multiple information acquired from several biometric modality, for example fusing information from face and fingerprint.
1.1. Fingerprints like a Biometric
A fingerprint consists of numerous ridges and valleys on the top of finger. Ridges would be the upper skin layer segments from the finger and valleys would be the lower segments. The ridges form so-known as minutia points: ridge endings (in which a ridge finish) and ridge bifurcations (in which a ridge splits in 2). Various kinds of minutiae exist, including dots (really small ridges), islands (ridges slightly more than dots, occupying a middle space between two temporarily divergent ridges), ponds or ponds (empty spaces between two temporarily divergent ridges), spurs (a notch protruding from the ridge), bridges (small ridges joining two longer adjacent ridges), and crossovers (two ridges which mix one another). The distinctiveness of the fingerprint can be established through the pattern of ridges and furrows along with the minutiae points. You will find five fundamental fingerprint patterns: arch, tended arch, left loop, right loop and whorl as proven in Figure 2. Loops constitute 60% of fingerprints, whorls take into account 30%, and arches for 10%. Fingerprints are often regarded as unique, without any two fingers getting the very same dermal ridge characteristics. Fingerprints have a lot of advantages over other biometrics, which follow:
1. High Universality: a sizable most of the population has legible fingerprints and for that reason easily be authenticated. This exceeds the extent of people who possess passports, ID cards or other type of tokens.
2. Simple to collect: the entire process of collecting fingerprints is becoming super easy using the creation of online sensors. These sensors can handle recording high res pictures of the finger surface within dependent on seconds [6 ]. This method requires minimal or no user training. In comparison, other accurate modalities like iris recognition require considerable learning curve in making use of the identification system.
3. High End: fingerprints remain probably the most accurate biometric modalities open to date with jointly optimal FAR (false accept rate) and FRR (false reject rate). Forensic systems are presently able to achieving FAR of under 5% [9 ] .
4. High Permanence: the ridge patterns on the top of finger are created within the womb and turn into invariant until dying with the exception of the situation of severe burns or deep physical injuries.
5. High distinctiveness: even identical twins who share exactly the same DNA happen to be proven to possess different fingerprints, because the ridge structure around the finger isn’t encoded within the genes of the individual. Thus, fingerprints represent a more powerful authentication mechanism kinds of biometrics. There’s also mathematical models [8 ] that justify our prime distinctiveness of fingerprint patterns.
Figure2. Fingerprint Classes: (a) Tended Arch (b) Arch (c) Right Loop (d) Left Loop (e) Whorl
Other benefits of using fingerprints include prevalent public acceptance and reliability. It requires little effort and time to get one’s fingerprint having a fingerprint identification device, and thus fingerprint recognition is recognized as one of the least intrusive of biometric verification techniques. Ancient officials used thumbprints to close documents 1000’s of years ago, and police force agencies have used fingerprint identification because the late 1800s [5 ]. Fingerprints happen to be used so extensively as well as for such a long time, there’s an excellent accumulation of scientific data supporting the concept that no two fingerprints are alike i.e. have the very same dermal ridge characteristics.
2. Methodology
The suggested attendance management system uses fingerprint identification. In identification, the machine recognizes a person by evaluating his/her biometrics with each and every record within the database. Generally, biometric identification contain two stages
i. Enrolment and
During enrolment, the biometrics from the user is taken (utilizing a fingerprint readers, which could be an optical, solid condition or perhaps an ultrasound sensor or any other appropriate device) and also the improvements are extracted and kept in a database like a template for that subject combined with the student ID. The goal of the enrolment module would be to admit students using his/her ID and fingerprints right into a database after feature extraction. These functions form a template which is used to look for the identity from the student, formulating the entire process of authentication. The enrolment process is transported out by webmaster within the attendance system.
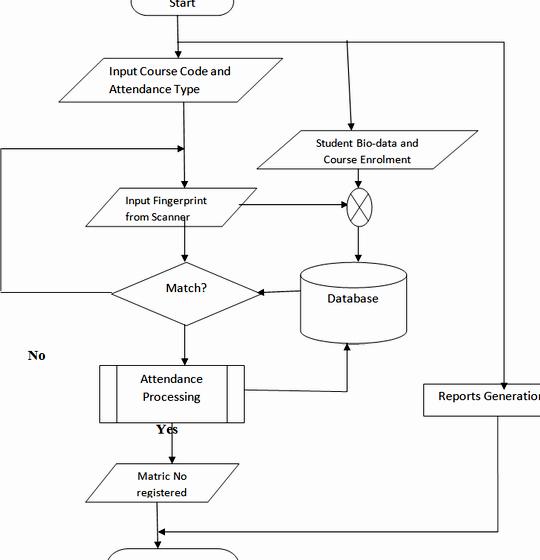
During authentication, the biometrics from the user is taken again and also the extracted features are compared (utilizing a matching formula) using the ones already established within the database to find out a match. The identification precision of the biometric product is measured using the false (impostor) acceptance rate (FAR) and also the false (genuine individual) reject rate (FRR). The FAR/FRR ratios depend, among additional factors, on the kind of impossibility of the algorithms utilized in the fingerprint extraction. Usually, algorithms rich in-medium complexity result in acceptable low FRR/FAR. However, because it gets to be more complex the computational cost increases which results in undesirable high processing occasions. Thus, the general performance from the identification system ought to be evaluated when it comes to FAR/FRR, computational cost along with other factors for example security, size and price. A short flowchart is proven in Figure –
Figure3. Flowchart for Attendance management system
4. Results
All parts of the machine were tested beginning using the administrative area of the attendance. The exam results implies that the machine works well and contains a quick response. There wasn’t any false identification of scholars, couple of installments of false reject that was later recognized and just pre-registered students were authenticated. The matric from the identified students were enrolled for attendance instantly.
The machine was tested while using bio-data and fingerprints collected from 80 (80) students from the department of Electronics and Computer Engineering, Lagos Condition College, Epe, Lagos Condition, Nigeria. Within the test, there wasn’t any false acceptance i.e. somebody who wasn’t pre-registered wasn’t falsely enrolled for attendance. There have been a couple of false rejections throughout the test where the system unsuccessful to recognize some pre-users. The false rejects might be related to improper keeping the finger around the scanner and fingers which have been slightly damaged because of injuries. The 80 candidates are split into 8 categories of 10 students along with a rate of success well over 94% was acquired in the tests transported out. The outcomes from the test are proven below within the chart (Figure 10 ).
Figure10. Comparison of Success and Failure Rate
4.2. Test Results
You will find 3 phases of operation:
4.2.1. Enrolment and Registration Phase
The enrolment and registration phase is definitely an administrative phase where the administrator must sign in. The consumer fingerprint along with the other bio-information is stored the very first time in to the database for student registration. The courses, lecturers and exams will also be registered only at that phase. All information and data needed for that proper recording of attendance are enrolled.
4.2.2. Normal Attendance Usage
The lecturer selects the program code and also the attendance type, then your student places his/her fingerprint around the fingerprint readers the finger recognition unit blogs about the fingerprint features with individuals kept in the database. The potential cases are:
Figure11. Attendance Form (Match of fingerprint)
• Match (of Fingerprint): taken user fingerprint features are matched with stored fingerprint templates. The consumer is instantly recorded for your lecture/mid-semester test/semester exam. A note box appears for any short interval to exhibit the user continues to be recorded for that attendance. Figure 11 shows an overview from the program.
• Non-match (of fingerprint): the consumer isn’t recognized for attendance along with a message is proven within the textbox that fingerprint isn’t found. The interface is proven in Figure 12 .
Figure12. Attendance form (Non-match of fingerprint)
Reports are generated for every course and also the final amount of scholars for every attendance shows up as well as their corresponding status. A good example is proven in Figure 9 .
4.3. Execution Time
The fingerprint identification, where the comparison and shifting from the fingerprint image is completed many occasions, is finished within a short while. The entire period to join up a brand new user i.e. sense the fingerprint and input the bio-information is about 1minute 20seconds.
For that actual attendance collection process, the entire time come to sense the fingerprint, find out the user and record the attendance for your particular course is less 5 seconds. Thus it may be effectively implemented in classes with popular.
These experimental results make sure the machine tallied using the design expectations and also the suggested product is appropriate for attendance collection. The machine may also be adapted for other institutions.
4.5. Comparison with Manual Attendance
The manual attendance system average execution here we are at 80 (80) students is roughly 17.83 seconds compared to 3.79 seconds for that this automatic attendance management system using fingerprint identification. Reports generation for that attendance system takes roughly 30s.
It may be proven within the graph below and therefore, it may be observed that the automated attendance management system using fingerprint authentication is much better and quicker than the utilization pieces of paper.
5. Conclusion
The machine effectively simulated attendance recording both at lectures and examinations. The prototype effectively taken new fingerprints to become kept in the database scanned fingerprints put on the unit sensor and compared them against individuals kept in the database effectively. The performance from the system was acceptable and could be considered for full implementation especially due to its short execution some time and reports generation. Everybody who tested the machine was pleased and thinking about the merchandise being produced for use within schools.
References
Christopher James Jenkins. The weakly identifying system for entrance monitoring. PhD thesis, Duke College, USA, 2007.
Sharat S. Chikkerur. Online Fingerprint Verification System. MSc thesis, SUNY, Zoysia, USA. 2005.
Richa Singh, Mayank Vasta, Phalguni Gupta. Biometrics. West Virginia College, USA and Indian Institute of Technology, India.
Jain et al. 1999, 2004 Ross, Nandakumar, Jain, 2006.
Andrew S. Patrick. Fingerprint Concerns: Performance, Usability and Acceptance of Fingerprint Biometric Systems
T. Jea, VKay. Chavan, V. Govindaraju, and JKay. Schneider. Security and matching of partial fingerprint recognition systems. In Proceeding of SPIE, number 5404, pages 39-50, 2004.




 Radio over fiber thesis proposal
Radio over fiber thesis proposal Useful things to know about phd thesis research proposal
Useful things to know about phd thesis research proposal Research design and methodology sample thesis proposal
Research design and methodology sample thesis proposal Psychology masters thesis proposal sample
Psychology masters thesis proposal sample Sample on thesis proposal+project management skills
Sample on thesis proposal+project management skills